This simple time-saving trick can thwart a devastating cyber-attack.
How often do you find yourself staring at a login screen, trying to remember what special character did you add to your pet’s name so that you can log in to a website? If you are the 65% of people who do not use a password manager, you do this fairly often. You spend hours of your life resetting passwords, getting side-tracked, forgetting your new password, and repeating the process. What a waste of time! If you are not using a password manager, you are more than likely helping attackers break into your accounts.
Why am I mentioning this as a blog post for an organization that deals with enterprise security? Well, having good operational security at home and good password hygiene carries over to the workplace. Having and using special and unique passwords starts with repetition and habit and once you start using a password manager at home for personal items you will more than likely find that you cannot function at work without a separate password manager there too. Again, the key here is separate; be sure to follow your organization's rules for approved software and keep your work passwords separate from your passwords.
Attacks known as “credential-stuffing” take advantage of individuals that reuse passwords from different logins and websites. Frequently stolen from a data breach, attackers attempt to use those same usernames and passwords on new sites they would like to gain access to. Furthermore, these attacks are not executed one at a time with just one username and password, instead, they are often automated, running thousands of attempts per second and run through large volumes of compromised computers - such as botnets.
Now, for those of you who have not yet connected the dots, adversaries take advantage of the vulnerability of us as humans having to remember all our passwords. We re-use them. Big deal, right? In a perfect world, our passwords are guarded by the organizations we log into and not shared with anyone else. In this perfect world, credential-stuffing attacks would not exist. Unfortunately, the reality is we live in a world where “data breach” is a household term. Organizations get breached. Sometimes this leads to username and password combinations from these sites making it into adversaries’ hands.
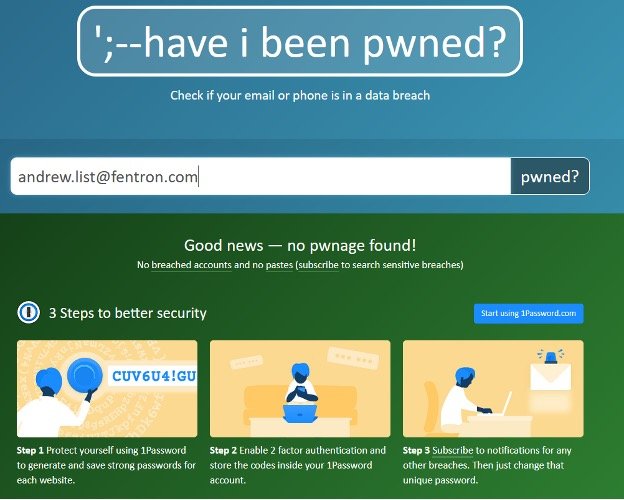
Monitoring data breaches is not easy, but solutions organizations such as “Have I been Pwned” [https://haveibeenpwned.com/] help users ascertain if they have been a part of any significant breaches.
Sometimes you are lucky and you have not been part of a breach yet. Other times…not so much.
You can subscribe to these sites as an individual or organization and receive breach reports as the website becomes aware of them. “Have I been Pwned” is free but encourages donations. It is maintained by Microsoft Regional Director and security speaker Troy Hunt.
During my time as a defender of organizations, I have seen credential-stuffing attacks first-hand. They can damage both the companies that catch the activity and their customers who have their accounts taken over. Once an attacker gains access to the account, they look for some way to monetize it. They often sell the stolen credentials to websites on the dark web anywhere from a few cents to a few dollars, earning the adversary money. The below image is an example of a dark web marketplace that can exchange money for accounts.
I cannot just leave you with a significant problem. As a fan of the free, cheap, and easy I want to provide you with a way to stop this type of attack. The solution I am proposing is something that I have been using since 2014.
Password managers – These things are amazing (in my humble opinion!). They store all your passwords and can generate pseudo-random passwords for you with enough complexity that they are tough to crack. The superpower of the password manager is that you can now create a special and unique password for each website or login that you need to remember and put an end to credential-stuffing attacks (well at least for you).
Password cracking is a talk for another day, but just understand that the more “keyspace” - a.k.a. the more distinct types of keys you use on the keyboard such as digits 1234, special characters, and punctuation @^%*(). - the better your password stands up to being guessed. While shortcuts like the XKCD “Correct Horse Battery Staple” are good for some things, they are flawed given some password guessing algorithms look for this tactic. If you are ever curious (you should be!) about how long it would take to crack a password, you can play around here: [https://www.security.org/how-secure-is-my-password/]. My advice: never enter real passwords. This is the internet, and who knows where the information you enter goes?
But I am going off the deep end here… Back to the problem at hand.
Password managers come in two major flavors – paid and free. Use whichever one makes you happy and works for you\. I am always a fan of free. My favorite - and again one that I have trusted since 2014 - has been KeePass here at keepass.info. It is a simple password manager that does truly encrypt all your passwords into one file that you can store locally on your computer or in the cloud storage of your choice. You can use utilities on your mobile devices or your computer (also free) to access and update your password manager with new passwords.
There are others such as OnePass, Dashlane, and LastPass. These are all great solutions that cost $$ with yearly subscriptions. Many of these solutions solve the issue of storing your passwords in their cloud-based solution and are available anywhere you have internet. Some also give you the option of downloading a local copy onto your device so you can access it without an internet connection. The key here is to make the commitment, choose one, and stick to it.
Once you start using a password manager, you will have the added benefit of getting back all the time that you would normally have spent resetting your passwords. You will take that necessary step of being more organized and there will be fewer barriers to just getting things done, less frustration, and more time spent on what matters.
Password managers do not come without some common complaints. So here is a list of common criticisms along with my responses:
1. If your password manager only depends on one password, won’t adversaries crack that one password and have access to all your important passwords, like finding that spot in your house that has all the keys?
response: Yes; your database of passwords is indeed secured with] just one password. So, it is important to make that password as secure as you can while still remembering it. I always recommend 25-character minimum passwords that include upper-case, lower-case, numbers, and special characters. (This recommendation is a point in time that will expire after this blog post is published in May 2022).
While recognizing the potential vulnerability, password managers are still a better alternative to unencrypted text files or spreadsheets containing passwords. Even if using encrypted spreadsheets password managers offer the same level of security with even more features.
2. Solutions hosted on the Internet and within specific platforms are still vulnerable to attack because there is no completely secure platform
Response: This is true - there is no secure platform. However, I believe the risk of credential theft via password reuse is higher, more damaging, and occurs more often than platform attacks against password managers.
3. Password managers depend on the clipboard to copy and paste your passwords and an attacker can take advantage of reading clear-text passwords in random access memory.
Response: yes, I’ll admit that this is a vector that adversaries can use along with other common ways of stealing passwords such as keyloggers. Mimikatz, the dreaded password stealing tool, also operates in computer memory space and there is little we can do to keep this information out of it. Password manager developers have started looking into ways of scrambling or mixing up the order of passwords in memory to make capturing this information less useful, but it will always be a cat-and-mouse game between adversaries and users.
Secondly: password managers work best to thwart external attacks rather than those [local] attacks that happen on the end-user's machine. We could have an entire discussion about attacks that cross that barrier. Who knows, it may be in our next blog post. Stay tuned for more…